Snoopers Charter
Discussion
sorry forgot to mention what 'droplet' referred to!! ( thanks bga )
https://www.digitalocean.com/pricing/
you can also host it outside the EU on their servers.
if you make a half-hearted effort to look, you can get a promo voucher for a $10 free credit too.
https://www.digitalocean.com/pricing/
you can also host it outside the EU on their servers.
if you make a half-hearted effort to look, you can get a promo voucher for a $10 free credit too.
SystemParanoia said:
sorry forgot to mention what 'droplet' referred to!! ( thanks bga )
https://www.digitalocean.com/pricing/
you can also host it outside the EU on their servers.
if you make a half-hearted effort to look, you can get a promo voucher for a $10 free credit too.
OK tell me more. Is this like a home brew VPN then or am I misunderstanding stuff? What's the advantage and disadvantage of using that over an off-the-shelf package from Cyberghost, for example?https://www.digitalocean.com/pricing/
you can also host it outside the EU on their servers.
if you make a half-hearted effort to look, you can get a promo voucher for a $10 free credit too.
All that jazz said:
OK tell me more. Is this like a home brew VPN then or am I misunderstanding stuff? What's the advantage and disadvantage of using that over an off-the-shelf package from Cyberghost, for example?
you setup thedroplet with ubuntu https://www.digitalocean.com/products/linux-distri... .. then run Streisand https://github.com/jlund/streisand from github on it.
and then you connect all of your\your families\friends\people you care about's devices through that vpn.
the difference is more than just having control.
you can also open up peer to peer communication within the vpn and have all of your devices locally* networked at all times and segment that network into layers of trust, or isolated in a virtual dmz for those you dont, or any you jus want to keep protected from everything.
you are less likely to get throttled by your isp too as they don't know what you're doing, only that you're doing it.
finally, you have the flexibility to do whatever you want with it without having to trust if 'cyberghost' aren't going to profile your traffic and inject ads/malware or sell off your info to make a quick buck later on.
or worry if they will submit all your identifiable data to whatever enforcement company come-a-knocking
you can also control what ports your tunnels run on to defeat known local defences. port 53 is nice.
finally having a server in the cloud lets you do fun stuff like ipv4 over dns which is near unstoppable in practice. https://github.com/yarrick/iodine
orther uses of far away servers can include trying out bleeding edge ideas like a ping based filesytem https://github.com/yarrick/pingfs ... anyone know the ip address of the ISS ?

Edited by SystemParanoia on Tuesday 6th December 20:15
Still confused. If you're setting it up at your home then surely you are still on the same IP as you would be normally and even though they can't see what you're doing it's still your name on the account. I don't see how adding a machine in-line running a VPN is going to change anything. Likewise if you use one of their VPNs why is that better than use any of the other VPN services like Cyberghost? You're still relying on them to keep their word when they say no logs and they won't hand over any info they have on you.
Also it's on Linux which is no good for the vast majority of us that run Windows.
Also it's on Linux which is no good for the vast majority of us that run Windows.
All that jazz said:
Still confused. If you're setting it up at your home then surely you are still on the same IP as you would be normally and even though they can't see what you're doing it's still your name on the account. I don't see how adding a machine in-line running a VPN is going to change anything. Likewise if you use one of their VPNs why is that better than use any of the other VPN services like Cyberghost? You're still relying on them to keep their word when they say no logs and they won't hand over any info they have on you.
Also it's on Linux which is no good for the vast majority of us that run Windows.
The os is immaterial, all web traffic is based on ipv4 or 6/dns requests and packet transfer.Also it's on Linux which is no good for the vast majority of us that run Windows.
having the vpn means that your isp does not get to see your DNS requests or the traffic sent along the wire.
when mr jobsworth comes along to snoop on you all he sees is garbled rubbish ( encryption of the vpn )
what mr jobsworth does see is that all of your traffic for all devices he knows about ( mobile operators have to give u their data too ) are all only connecting to one single ip address ( your VPN )
Your VPN hosted on your droplet is by defaut setup to not store any logs, you can destroy it at a moments notice as if it had never existed.
Running the vpn, to all external sites and services you appear to be originating from the VPN ip address, and your own is masked and hidden from those who would try to track you via cookies and javascript applets and such.
my explanations are really bad. how about a picture
http://manurevah.com/blah/en/blog/ISP-vs-VPN-vs-To...
Regular internet access - unencrypted - ISP sees everythnig
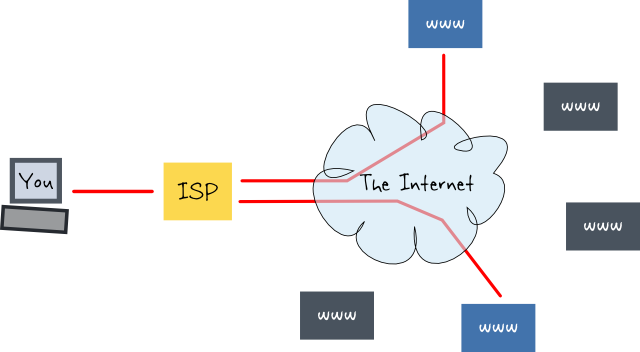
VPN internet, isp only sees you connect to one ip address in the 'cloud' and cant see what is being sent or where the traffic goes beyond that point
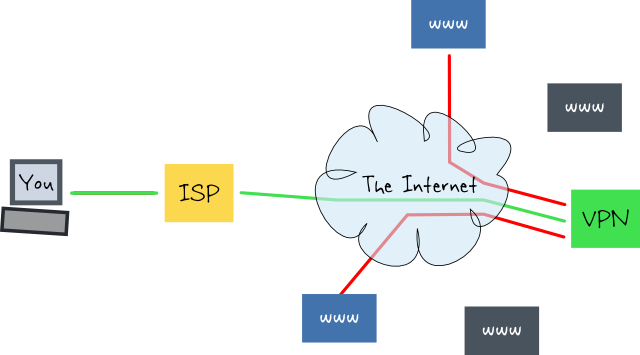
the benefit is that you control that cloud node, and with one button press you can make it not exist and so there is nothing to be 'found' that can be used against you somehow
Edited by SystemParanoia on Tuesday 6th December 20:43
I still don't see how this is doing anything different from a no-logs VPN service. The only difference is it's in your front room and not (eg.) Romania. You've still got to pay for the Cloud server to run it which actually works out more expensive that the VPN service. The only difference I'm seeing is that theoretically you have control of the logs, however if for example you were on a kiddy fiddling site that was being monitored by the feds, how is the VPN IP on the machine you're running it through in your front room going to be hidden from them?
All that jazz said:
I still don't see how this is doing anything different from a no-logs VPN service. The only difference is it's in your front room and not (eg.) Romania. You've still got to pay for the Cloud server to run it which actually works out more expensive that the VPN service. The only difference I'm seeing is that theoretically you have control of the logs, however if for example you were on a kiddy fiddling site that was being monitored by the feds, how is the VPN IP on the machine you're running it through in your front room going to be hidden from them?
But it's not in your front room, is it?All that jazz said:
I still don't see how this is doing anything different from a no-logs VPN service.
It's very similar.All that jazz said:
The only difference is it's in your front room and not (eg.) Romania.
No, the VPN server isn't in your front room. It's very much the same concept.All that jazz said:
You've still got to pay for the Cloud server to run it which actually works out more expensive that the VPN service.
Does it? $5 a month is pretty cheap.All that jazz said:
The only difference I'm seeing is that theoretically you have control of the logs, however if for example you were on a kiddy fiddling site that was being monitored by the feds, how is the VPN IP on the machine you're running it through in your front room going to be hidden from them?
The VPN IP isn't hidden from them. But the idea is that UK authorities only see encrypted traffic to the VPN IP and the VPN is in a territory they don't have authority in.the address doesnt need to be hidden cause all the traffic between you and the vpn is encrypted.
traffic from the vpn onwards isnt.
( if you're on a kiddy fiddler site you deserve to be burned alive, but that's another issue for another thread )
free VPN will hide your traffic yes. but do you trust them ? do you trust then not to hand over the logs that your isp couldent if asked by the authorities?
I dont. ill trust myself, and my own servers.
traffic from the vpn onwards isnt.
( if you're on a kiddy fiddler site you deserve to be burned alive, but that's another issue for another thread )
free VPN will hide your traffic yes. but do you trust them ? do you trust then not to hand over the logs that your isp couldent if asked by the authorities?
I dont. ill trust myself, and my own servers.
This whole thing is actually mental beyond belief.
The snoopers charter storing our history and the BBFC deciding what sort of smut adults are 'allowed' to watch is just so ridiculous I don't know where to start.
Anyone who says they wouldn't mind their browsing history being made public is either lying, or living a staggeringly 'vanilla' existence.
The snoopers charter storing our history and the BBFC deciding what sort of smut adults are 'allowed' to watch is just so ridiculous I don't know where to start.
Anyone who says they wouldn't mind their browsing history being made public is either lying, or living a staggeringly 'vanilla' existence.
I still don't get it  . Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare machine running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
. Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare machine running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
 . Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare machine running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
. Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare machine running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?The VPN you have bought encrypts the connection between your machine and their server, wherever cyberghost host, and you choose the country exit point. That's what you currently have.
What SP is suggesting is that instead of paying someone else to run the VPN system for you, you do it yourself and rent a 'slice' of server capacity to do so. You set the VPN endpoint up and choose 'no logs'. That way you know that no logs are being kept.
The rest is the same for both of them: The link between your system and the VPN server is still secure, ISP still only see encrypted traffic so can only tell that you're going to <ip address> in <country that UK gov't has no jurisdiction> so the *actual* traffic where it pops out can't be logged as it's already beyond the reach of the ICR's remit..
What SP is suggesting is that instead of paying someone else to run the VPN system for you, you do it yourself and rent a 'slice' of server capacity to do so. You set the VPN endpoint up and choose 'no logs'. That way you know that no logs are being kept.
The rest is the same for both of them: The link between your system and the VPN server is still secure, ISP still only see encrypted traffic so can only tell that you're going to <ip address> in <country that UK gov't has no jurisdiction> so the *actual* traffic where it pops out can't be logged as it's already beyond the reach of the ICR's remit..
All that jazz said:
I still don't get it  . Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
. Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
the droplet / AWS / azure instance is nothing more than a virtual container within a larger virtual host sitting in some monstrous data centre somewhere. . Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
. Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?you also have the option of 'colocating' - that is where you buy and prep a machine and then pay to have it sit in some monstrous data centre, then you only really pay for power and monthly traffic allowance, and occasionally have some I.T bod walk over and power cycle it when you've really messed up

Tonsko said:
The VPN you have bought encrypts the connection between your machine and their server, wherever cyberghost host, and you choose the country exit point. That's what you currently have.
What SP is suggesting is that instead of paying someone else to run the VPN system for you, you do it yourself and rent a 'slice' of server capacity to do so. You set the VPN endpoint up and choose 'no logs'. That way you know that no logs are being kept.
The rest is the same for both of them: The link between your system and the VPN server is still secure, ISP still only see encrypted traffic so can only tell that you're going to <ip address> in <country that UK gov't has no jurisdiction> so the *actual* traffic where it pops out can't be logged as it's already beyond the reach of the ICR's remit..
And where is the server capacity coming from? Would that be an unknown third party that requires your bank/card details and personal information, per chance?What SP is suggesting is that instead of paying someone else to run the VPN system for you, you do it yourself and rent a 'slice' of server capacity to do so. You set the VPN endpoint up and choose 'no logs'. That way you know that no logs are being kept.
The rest is the same for both of them: The link between your system and the VPN server is still secure, ISP still only see encrypted traffic so can only tell that you're going to <ip address> in <country that UK gov't has no jurisdiction> so the *actual* traffic where it pops out can't be logged as it's already beyond the reach of the ICR's remit..
SystemParanoia said:
All that jazz said:
I still don't get it  . Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
. Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
the droplet / AWS / azure instance is nothing more than a virtual container within a larger virtual host sitting in some monstrous data centre somewhere. . Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?
. Explain to me the physical properties of the VPN server, who owns it, which parties have access/control of it. I'm imagining you use a spare machine to act as the VPN server in order to fulfil the bit about being able to delete your own logs. So this is presumably connected to your router. If you visit some dodgy site that's being monitored by the feds then that site is going to have an incoming IP address and by tracing the route back through the server network it's going to land in your front room where you have the spare running as the VPN server. What am I missing? If this is not the case then how is the VPN server IP and location completely hidden from the destination site?you also have the option of 'colocating' - that is where you buy and prep a machine and then pay to have it sit in some monstrous data centre, then you only really pay for power and monthly traffic allowance, and occasionally have some I.T bod walk over and power cycle it when you've really messed up

All that jazz said:
Tonsko said:
The VPN you have bought encrypts the connection between your machine and their server, wherever cyberghost host, and you choose the country exit point. That's what you currently have.
What SP is suggesting is that instead of paying someone else to run the VPN system for you, you do it yourself and rent a 'slice' of server capacity to do so. You set the VPN endpoint up and choose 'no logs'. That way you know that no logs are being kept.
The rest is the same for both of them: The link between your system and the VPN server is still secure, ISP still only see encrypted traffic so can only tell that you're going to <ip address> in <country that UK gov't has no jurisdiction> so the *actual* traffic where it pops out can't be logged as it's already beyond the reach of the ICR's remit..
And where is the server capacity coming from? Would that be an unknown third party that requires your bank/card details and personal information, per chance?What SP is suggesting is that instead of paying someone else to run the VPN system for you, you do it yourself and rent a 'slice' of server capacity to do so. You set the VPN endpoint up and choose 'no logs'. That way you know that no logs are being kept.
The rest is the same for both of them: The link between your system and the VPN server is still secure, ISP still only see encrypted traffic so can only tell that you're going to <ip address> in <country that UK gov't has no jurisdiction> so the *actual* traffic where it pops out can't be logged as it's already beyond the reach of the ICR's remit..
Have a readup on crypto currency
Gassing Station | News, Politics & Economics | Top of Page | What's New | My Stuff




 .
.